In the digital age, cybersecurity is not just a buzzword; it’s a necessity. With cybercriminals becoming more sophisticated, it’s crucial to stay one step ahead. That’s why we’re revealing a simple penetration testing trick that has hackers running scared. This trick is so effective, it’s become the secret weapon of cybersecurity experts worldwide.
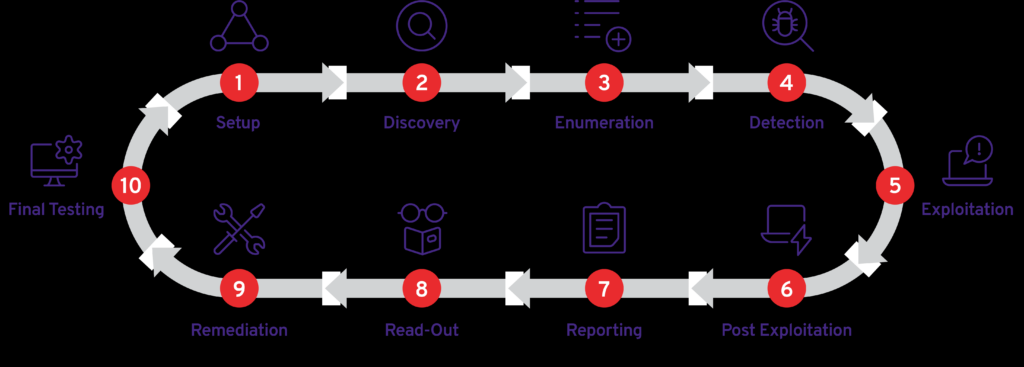
The Cybersecurity Landscape
Before we dive into the trick, let’s set the stage. Cybersecurity is the art of protecting networks, devices, and data from unauthorized access or criminal use and ensuring confidentiality, integrity, and availability of information. It’s a field that’s constantly evolving, with new threats emerging daily. That’s why penetration testing, also known as ethical hacking, is a critical component of any robust cybersecurity strategy
Penetration Testing: Your Cybersecurity Guardian
Penetration testing is the practice of testing a computer system, network, or web application to find vulnerabilities that an attacker could exploit. It’s like hiring a professional burglar to find the weaknesses in your home security system before the real burglars do.
The One Trick That Changes Everything
Now, for the moment you’ve been waiting for: the trick that’s causing a stir in the hacker community. It’s called Social Engineering Penetration Testing. This method replicates how cyber-criminals target employees to gain privileged access to protected systems and information.
The Steps Involved:
- Tailgating: The tester follows employees into secure areas without proper authentication.
- Pretexting: The tester impersonates an employee to persuade others to divulge confidential information.
- Baiting: The tester leaves malware-infected USB keys for employees to find and use, simulating a USB Drop attack.
Why Hackers Despise This Trick
Hackers hate social engineering penetration testing because it exposes their favorite tactics. By understanding and anticipating these human-centric attacks, organizations can train their staff to be the first line of defense against cyber threats.
Implementing the Trick in Your Organization
To implement this trick, start with awareness. Educate your employees about the common tactics used by social engineers. Conduct regular training sessions and simulations to ensure everyone is prepared to spot and stop these attacks.
The Impact on Your Cybersecurity Posture
By incorporating social engineering penetration testing into your cybersecurity strategy, you’ll achieve:
- Enhanced Security Awareness: Employees become vigilant and proactive in identifying suspicious behavior.
- Reduced Risk of Data Breaches: With fewer human errors, the likelihood of successful attacks plummets.
- Compliance and Trust: Demonstrating a commitment to security builds trust with customers and complies with regulations.
Conclusion: Your Data, Secured
Cybersecurity is a battle of wits between defenders and attackers. By mastering this simple penetration testing trick, you’re not just protecting data; you’re safeguarding the future of your organization. Hackers hate him, but you’ll love the peace of mind that comes with knowing your data is secure.
Don’t wait for a breach to happen. Take action now, and join the ranks of cybersecurity experts who are turning the tables on cybercriminals. Your data deserves the best defense, and now you have the knowledge to provide it.
Embrace this trick, and you’ll not only frustrate hackers but also fortify your digital fortress. Remember, in the world of cybersecurity, knowledge is power, and now you’re empowered to protect what matters most.
1: The Ultimate Guide to Penetration Testing
2: A Complete Guide to Cyber Security Penetration Tests
3: The Complete Guide To Penetration Testing
Frequently Asked Questions (FAQs) :Simple Penetration Testing Trick to Protect Your Data
1. What is cybersecurity, and why is it important in the digital age?
Cybersecurity involves protecting networks, devices, and data from unauthorized access or criminal use. In the digital age, with cybercriminals becoming more sophisticated, cybersecurity is crucial to ensure confidentiality, integrity, and availability of information.
2. What is penetration testing, and why is it essential in cybersecurity?
Penetration testing, also known as ethical hacking, is the practice of testing computer systems, networks, or web applications to find vulnerabilities that attackers could exploit. It helps organizations identify weaknesses before malicious actors do, thus strengthening their security posture.
3. What is the one trick mentioned that has hackers running scared?
The trick causing a stir in the hacker community is called Social Engineering Penetration Testing. It replicates how cybercriminals target employees to gain privileged access to protected systems and information.
4. What are the steps involved in Social Engineering Penetration Testing?
The steps include tailgating (following employees into secure areas without proper authentication), pretexting (impersonating an employee to persuade others to divulge confidential information), and baiting (leaving malware-infected USB keys for employees to find and use).
5. Why do hackers despise Social Engineering Penetration Testing?
Hackers dislike this method because it exposes their favorite tactics. By understanding and anticipating these human-centric attacks, organizations can train their staff to be the first line of defense against cyber threats.
6. How can organizations implement this trick in their cybersecurity strategy?
Organizations can start by raising awareness among employees about common tactics used by social engineers. Regular training sessions and simulations should be conducted to ensure everyone is prepared to spot and stop these attacks.
7. What impact does Social Engineering Penetration Testing have on an organization’s cybersecurity posture?
Implementing this trick enhances security awareness among employees, reduces the risk of data breaches by minimizing human errors, and helps in compliance with regulations, thereby building trust with customers.
8. How can individuals and organizations learn more about penetration testing?
There are various resources available, including guides such as “The Ultimate Guide to Penetration Testing,” “A Complete Guide to Cyber Security Penetration Tests,” and “The Complete Guide To Penetration Testing,” which provide comprehensive insights into penetration testing techniques and practices.
9. How does mastering Social Engineering Penetration Testing benefit organizations?
By mastering this trick, organizations not only protect their data but also safeguard their future. They frustrate hackers, fortify their digital defenses, and empower themselves to protect what matters most in the realm of cybersecurity.
10. What should organizations do to ensure their data remains secure in the face of evolving cyber threats?
Organizations should take proactive measures, embrace cybersecurity best practices, and continuously educate and train their employees to recognize and thwart social engineering attacks. Waiting for a breach to happen is not an option; action must be taken now to protect against cybercriminals.
