Introduction:
As we approach the year 2030, the world faces a multitude of challenges, from environmental concerns to technological disruptions. Among these challenges looms a threat that has been gaining increasing attention: the advent of quantum computing. In this blog post, we delve into the implications of quantum computing for data encryption and the urgent need for quantum-resistant security measures.
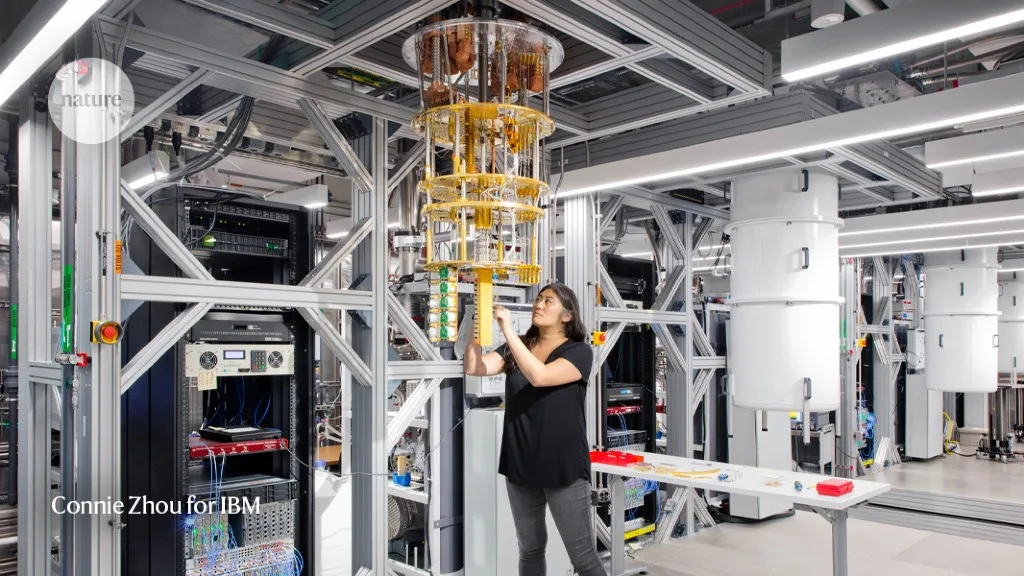
Table of Contents
The Rise of Quantum Computing:
In 2015, Google and NASA made a groundbreaking announcement regarding the development of quantum computers boasting an unprecedented number of qubits. These quantum computers possess computational power far surpassing that of classical computers, raising concerns about the potential vulnerabilities they introduce into data security frameworks. As companies race to commercialize quantum computers, the need for robust encryption methods becomes ever more pressing.
The Looming Threat to Data Security:
Central to the discussion of quantum computing’s impact is the role of cryptography in safeguarding sensitive information. Traditional encryption methods, such as those based on mathematical algorithms like AES, may prove inadequate in the face of quantum computing’s immense processing capabilities. This poses a significant risk to data security, as confidential information could be compromised if quantum computers can break encryption codes with ease.

Evolution of Encryption Algorithms:
To understand the magnitude of the challenge posed by quantum computing, it’s essential to trace the evolution of encryption algorithms over time. From ancient methods like the Caesar cipher to modern encryption standards like AES, encryption techniques have evolved to keep pace with technological advancements. However, the emergence of quantum computing necessitates a paradigm shift in encryption strategies, leading to the development of quantum-resistant algorithms based on lattice cryptography.

The Race for Quantum-Resistant Encryption:
Recognizing the urgency of the situation, organizations like the National Institute of Standards and Technology (NIST) have embarked on initiatives to develop post-quantum encryption standards. These standards aim to ensure that encryption methods remain secure even in the face of quantum computing’s disruptive capabilities. However, challenges remain in creating encryption algorithms that are truly quantum-resistant and capable of withstanding future advancements in quantum technology.
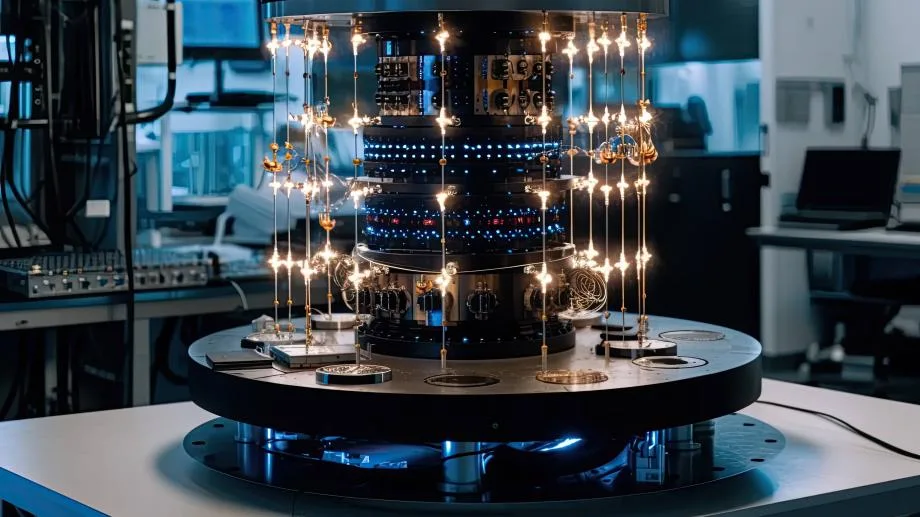
Ensuring Data Security in 2030 and Beyond:
As we approach the anticipated arrival of quantum computing in 2030, the need for robust cybersecurity measures has never been greater. Individuals, businesses, and government agencies must prioritize the adoption of quantum-resistant encryption methods to safeguard sensitive data. Moreover, ongoing research and collaboration will be essential in staying ahead of emerging threats and maintaining a secure digital ecosystem.
Conclusion:
The year 2030 holds the promise of transformative technological advancements, but it also brings unprecedented challenges to data security. Quantum computing represents a paradigm shift that demands a reevaluation of existing encryption methods and the development of quantum-resistant alternatives. By investing in innovative cybersecurity solutions and fostering collaboration across sectors, we can navigate the complexities of the digital landscape and ensure a secure future for generations to come. For more information, so please visit the following links.
IBM, Security Encryption, Deloitte
Frequently Asked Questions (FAQs) About Quantum Computing and Data Encryption:
1. What is quantum computing, and how does it differ from classical computing?
Quantum computing is a revolutionary approach to computation that utilizes the principles of quantum mechanics to perform operations on quantum bits (qubits), which can exist in multiple states simultaneously. This allows quantum computers to solve certain problems much faster than classical computers, which rely on binary bits that can only exist in one state at a time.
2. How does quantum computing affect data encryption?
Quantum computing poses a significant threat to traditional encryption methods used to secure sensitive data. The immense processing power of quantum computers enables them to quickly solve complex mathematical problems, such as factoring large prime numbers, which are the basis of many encryption algorithms. As a result, encrypted data that is considered secure against classical computers may be vulnerable to decryption by quantum computers.
3. What are quantum-resistant encryption algorithms, and why are they important?
Quantum-resistant encryption algorithms are cryptographic techniques designed to withstand attacks from quantum computers. These algorithms utilize mathematical structures, such as lattice-based cryptography, that are believed to be resistant to quantum computing attacks. Developing and implementing quantum-resistant encryption algorithms is crucial for maintaining data security in the era of quantum computing.
4. What efforts are underway to develop quantum-resistant encryption standards?
Organizations like the National Institute of Standards and Technology (NIST) are actively working to establish post-quantum encryption standards. NIST’s Post-Quantum Cryptography Standardization project aims to identify and standardize quantum-resistant encryption algorithms that can be implemented across various systems and applications.
5. How can individuals and organizations prepare for the impact of quantum computing on data security?
To mitigate the risks associated with quantum computing, individuals and organizations should stay informed about developments in quantum-resistant encryption and adopt best practices for cybersecurity. This may include updating encryption protocols, implementing multi-factor authentication, and investing in technologies that can detect and respond to potential security breaches.
6. Will existing encryption methods become obsolete with the advent of quantum computing?
While quantum computing has the potential to render some existing encryption methods vulnerable, it is unlikely to make all encryption obsolete overnight. However, there is a pressing need to transition to quantum-resistant encryption algorithms to ensure the long-term security of sensitive data in the face of advancing quantum technologies.
7. How can quantum computing benefit other fields besides cryptography?
Beyond data encryption, quantum computing holds promise for solving a wide range of complex problems in fields such as drug discovery, materials science, optimization, and artificial intelligence. By harnessing the unique capabilities of quantum computers, researchers hope to accelerate scientific discoveries and drive innovation across various industries.

